At the end of this page, you can find the full list of publications and patents.
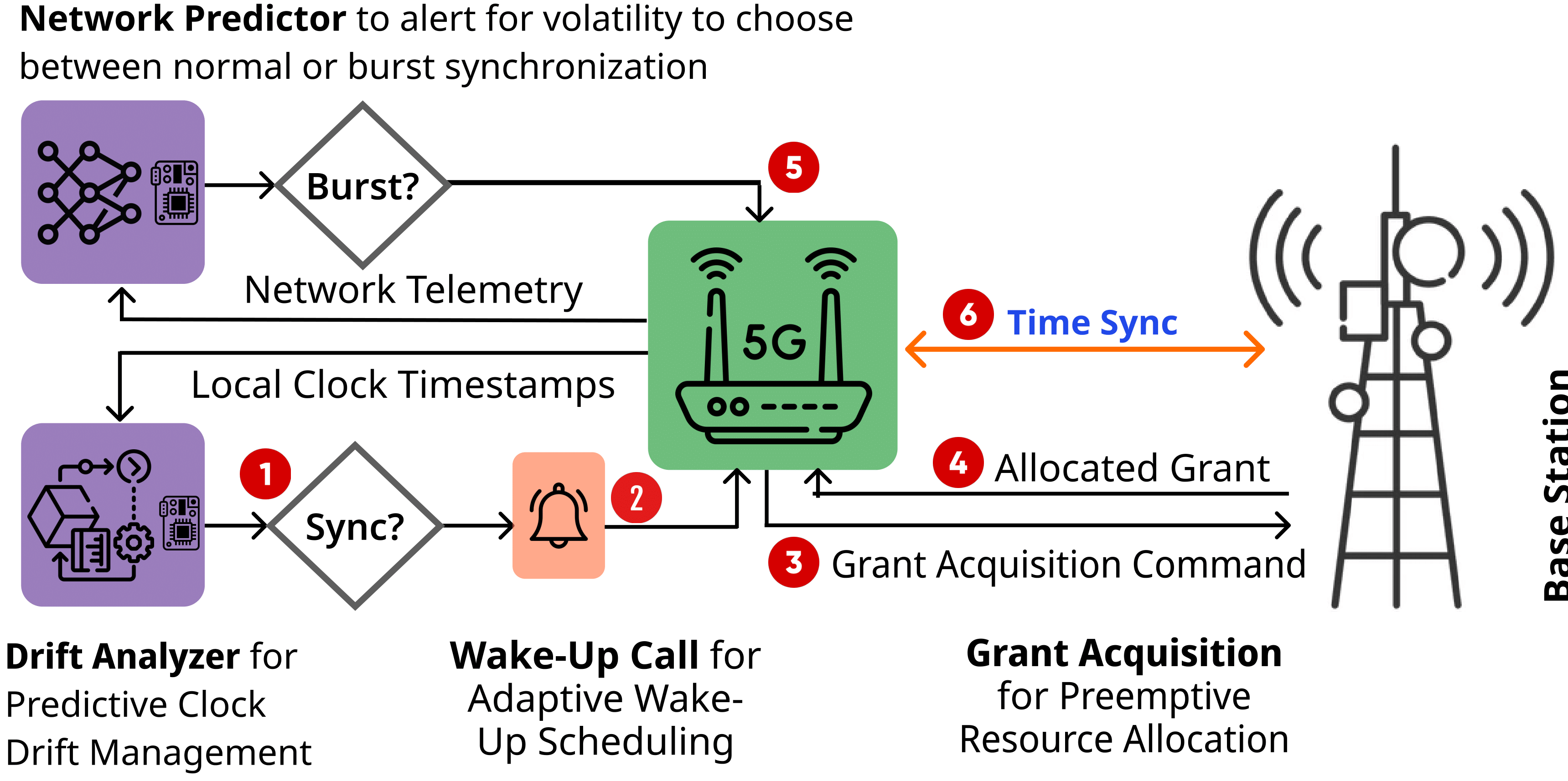
SynchroNB is an on-device framework that combines lightweight machine learning with a cross-layer control loop. It forecasts 5G network volatility and crystal drift to adaptively wake the cellular modem, reserves uplink resources just in time, switches into resilience mode when the wireless link degrades, and prioritizes time synchronization packets in the MAC-layer queue. Our experiments show that SynchroNB achieves single-millisecond-level synchronization accuracy under diverse wireless conditions, while requiring only 36% of the radio-on time and 25% of the bandwidth of the NTP baseline.
Muhammad Abdullah Soomro^, Muhammad Shayan Nazeer^, Collin DelSignore, Yasra Chandio, Muhammad Taqi Raza, and Fatima Muhammad Anwar
^ These authors contributed equally to this work.
This study investigates the effects of process automation on software development and the IT workforce. Through a mixed-methods approach, we analyze how automation tools influence productivity, job satisfaction, and skill requirements among IT professionals. Our findings reveal significant shifts in workflow dynamics and highlight the need for continuous learning and adaptation in the evolving tech landscape.
Yutong Liu, Matthew J. Hashim, Wei Chen, and Muhammad Taqi Raza
Americas Conference on Information Systems (AMCIS)

This paper presents the first systematic security analysis of in-flight Wi-Fi paywall systems, revealing vulnerabilities that allow covert channels, free Internet access, and bandwidth theft due to architectural and policy flaws. Countermeasures are proposed to address these issues.
Abdullah Al Ishtiaq^, Raja Hasnain Anwar^, Yasra Chandio, Fatima Muhammad Anwar, Syed Rafiul Hussain, and Muhammad Taqi Raza
^ These authors contributed equally to this work.
ACM Conference on Security and Privacy in Wireless and Mobile Networks (WiSec)
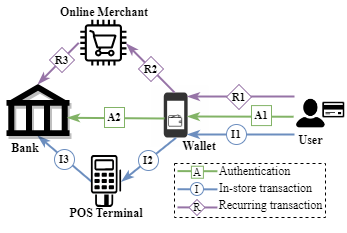
This paper investigates the security of digital wallet transactions, highlighting vulnerabilities in authentication, authorization, and access control. It exposes weaknesses in decentralized authority delegation, allowing attackers to add stolen bank cards, bypass payment authorization, and violate access control policies. The findings underscore the severity of these vulnerabilities, prompting proposed remedies to enhance security measures in digital wallet systems.
Raja Hasnain Anwar, Syed Rafiul Hussain, and Muhammad Taqi Raza

Driver distraction is one of the leading causes of accidents in semi-autonomous vehicles. We identify the relationship between the traffic event, the type of automotive sensing technologies, and its processing resources to capture that event to design the driver’s attention gauge.
Raja Hasnain Anwar, Fatima Muhammad Anwar, Muhammad Kumail Haider, Alon Efrat, and Muhammad Taqi Raza
International Conference on Modeling, Analysis and Simulation of Wireless and Mobile Systems (MSWiM)

We propose MalRNN, a novel deep learning-based approach to automatically generate evasive malware variants without any of these restrictions. Our approach features an adversarial example generation process, which learns a language model via a generative sequence-to-sequence recurrent neural network to augment malware binaries. MalRNN effectively evades three recent deep learning-based malware detectors and outperforms current benchmark methods.
Mohammadreza Ebrahimi, Ning Zhang, James Hu, Muhammad Taqi Raza, and Hsinchun Chen
2026: SynchroNB: Toward Robust Timing for 5G NB-IoT Networks
Muhammad Abdullah Soomro^, Muhammad Shayan Nazeer^, Collin DelSignore, Yasra Chandio, Muhammad Taqi Raza, and Fatima Muhammad Anwar
^ These authors contributed equally to this work.
ACM SenSys
2025: Impacts of Process Automation on Software Development and the IT Workforce
🏆 Best Paper Award
Yutong Liu, Matthew J. Hashim, Wei Chen, and Muhammad Taqi Raza
Americas Conference on Information Systems (AMCIS)
2025: Cloud Nine Connectivity: Security Analysis of In-Flight Wi-Fi Paywall Systems
Abdullah Al Ishtiaq^, Raja Hasnain Anwar^, Yasra Chandio, Fatima Muhammad Anwar, Syed Rafiul Hussain, and Muhammad Taqi Raza
^ These authors contributed equally to this work.
ACM Conference on Security and Privacy in Wireless and Mobile Networks (WiSec)
2025: PLCpot: Application Dialogue Replay based Scalable PLC Honeypot for Industrial Control Systems [PDF]
Syed Ali Qasim, Muhammad Taqi Raza, and Irfan Ahmed
16th ACM Conference on Cyber-Physical Systems (ICCPS)
2024: In Wallet We Trust: Bypassing the Digital Wallets Payment Security for Free Shopping [PDF] [Slides]
Raja Hasnain Anwar, Syed Rafiul Hussain, and Muhammad Taqi Raza
USENIX Security Symposium
2024: Characterizing Encrypted Application Traffic through Cellular Radio Interface Protocol [PDF] [Slides]
Md Ruman Islam, Raja Hasnain Anwar, Spyridon Mastorakis, and Muhammad Taqi Raza
IEEE International Conference on Mobile Ad-Hoc and Smart Systems (MASS)
2023: A Comprehensive Study on Cyber Attacks in Communication Networks in Water Purification and Distribution Plants: Challenges, Vulnerabilities, and Future Prospects
Muhammad Muzamil Aslam, Ali Tufail, Ki-Hyung Kim, Rosyzie Anna Awg Haji Mohd Apong, and Muhammad Taqi Raza
Sensors
2023: Redefining the Driver Attention Gauge in Semi-Autonomous Vehicles [PDF] [Slides]
Raja Hasnain Anwar, Fatima Muhammad Anwar, Muhammad Kumail Haider, Alon Efrat, and Muhammad Taqi Raza
International Conference on Modeling, Analysis and Simulation of Wireless and Mobile Systems (MSWiM)
2023: Detecting Privacy Threats with Machine Learning: A Design Framework for Identifying Side-Channel Risks of Illegitimate User Profiling [PDF]
Raja Hasnain Anwar, Yi (Zoe) Zou, and Muhammad Taqi Raza
Americas Conference on Information Systems (AMCIS)
2022: Enabling Emerging Edge Applications Through a 5G Control Plane Intervention
Mukhtiar Ahmad, Muhammad Ali Nawazish, Muhammad Taimoor Tariq, Muhammad Basit Iqbal Awan, Muhammad Taqi Raza, and Zafar Ayyub Qazi
International Conference on emerging Networking EXperiments and Technologies
2022: LTE NFV Rollback Recovery
Muhammad Taqi Raza, Zhowei Tan, Ali Tufail, and Fatima Muhammad Anwar
IEEE Transactions on Network and Service Management
2021: Keeping eyes on the road: the role of situated IS delegation in influencing drivers’ situational awareness [PDF]
Raja Hasnain Anwar, Yi (Zoe) Zou, and Muhammad Taqi Raza
International Conference on Information Systems (ICIS) TREOs
2021: On Key Reinstallation Attacks over 4G LTE Control-Plane: Feasibility and Negative Impact
Muhammad Taqi Raza, Yunqi Guo, Songwu Lu, and Fatima Muhammad Anwar
Annual Computer Security Applications Conference
2021: Highly Available Service Access Through Proactive Events Execution in LTE NFV
Muhammad Taqi Raza, Fatima Muhammad Anwar, Dongho Kim, and Kyu-Han Kim
IEEE Transactions on Network and Service Management
2020: Binary Black-box Evasion Attacks Against Deep Learning-based Static Malware Detectors with Adversarial Byte-Level Language Model
Mohammadreza Ebrahimi, Ning Zhang, James Hu, Muhammad Taqi Raza, and Hsinchun Chen
arXiv:2012.07994
2020: {FERRET}: Fall-back to {LTE} Microservices for Low Latency Data Access
Muhammad Taqi Raza, Fatima Muhammad Anwar, Dongho Kim, and Kyu-Han Kim
USENIX Workshop on Hot Topics in Edge Computing